As I mentioned in a previous post, there are many kinds of Site to Site VPNS that can be implemented on a cisco router.There are many resource materials on the internet on Basic Point-to-Point Site-to-Site IPSEC VPNS. I do not intend to add to the tons of materials already out there.GRE/IPSEC VPNS are implemented similarly as all traffic is passed through the GRE tunnel (encapsulated with GRE) and the GRE traffic is now encapsulated with IPSEC. Here the GRE traffic is the Interesting traffic.DMVPN involves setting up VPNS when they are needed between sites. This involves a combination of NHRP, mGRE, CEF and IPSEC. Petr Lapukhov, 4xCCIE, an instructor at INE has a detailed technical post on DMVPN, which can be found on the INE blog.Boštjan Šuštar also has another technical article on DMVPN that explains it from a real world perspective. It can be found at the NIL IPCorner. I strongly recommend that you go through both materials. I dont think I have anything to add to these; they have everything on DMVPNs covered :-)Besides, Boštjan was probably a CCIE before i could even spell a router ;)And now, GETVPN :-)GETVPN is cisco's new VPN technology (from IOS 12.4(6)T). The concept is simple.VPN Sites for an organisation are in a group. The group consists of one or more key servers (more than one key server is advised for redundancy).The group memers would request for the SAs from the server. The server is actually configured with all the SA parameters. the server just sends out the SA to the members, The server also sends the traffic to be considered INTERESTING to the members. they DO NOT negotiate SAs between each other. This Hub and spoke mechanism is used to download the SAs.The actual IPSEC communicaion occurs on a full mesh topology as the spokes just encrypt the traffic based on the information downloaded fron the key server.
Implementation:
Diagram:
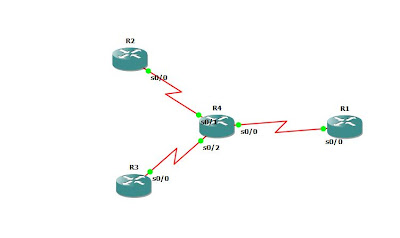
Basic Configuration
Key Server:conf t
hostname R1
interface Serial 0/0
ip address 172.16.14.1 255.2552.255.0
endGroup member 1
conf t
hostname R2
interface Serial0/0
ip address 172.16.24.2 255.255.255.0
end
interface Loopback0
ip address 192.168.2.1 255.255.255.0
endGroup Member 2
conf t
hostname R3
interface Serial0/0
ip address 172.16.24.2 255.255.255.0
end
int loopback 0
ip address 192.168.3.1 255.255.255.0
endServer Configuration;
access-list 103 permit ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255!crypto isakmp policy 10 encr 3des authentication pre-share group 2!crypto isakmp key cisco address 172.16.24.2crypto isakmp key cisco address 172.16.34.3!crypto ipsec transform-set TRANSF esp-3des esp-md5-hmac!crypto ipsec profile GETVPN set transform-set TRANSF!crypto gdoi group VPN identity number 1 ! server local ! rekey retransmit 10 number 3 registration interface Serial0/0 sa ipsec 10 ! profile GETVPN match address ipv4 103!Group Member Configuration (Identical on both sides):
crypto isakmp policy 10 encr 3des authentication pre-share group 2crypto isakmp key cisco address 172.16.14.1crypto gdoi group VPN identity number 1 server address ipv4 172.16.14.1crypto map GETVPN 10 gdoi set group VPNinterface s0/0crypto map GETVPNTest :-)
R2(config-if)#do sh cry ipsec sainterface: Serial0/0 Crypto map tag: GETVPN, local addr 172.16.24.2 protected vrf: (none) local ident (addr/mask/prot/port): (192.168.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (192.168.0.0/255.255.0.0/0/0) current_peer 172.16.14.1 port 848 PERMIT, flags={} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.16.24.2, remote crypto endpt.: 172.16.14.1 path mtu 1500, ip mtu 1500, ip mtu idb Serial0/0 current outbound spi: 0x38FEDAF9(956226297) inbound esp sas: spi: 0x38FEDAF9(956226297) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 5, flow_id: SW:5, crypto map: GETVPN sa timing: remaining key lifetime (k/sec): (4415223/1967) IV size: 8 bytes replay detection support: Y Status: ACTIVE inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0x38FEDAF9(956226297) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 6, flow_id: SW:6, crypto map: GETVPN sa timing: remaining key lifetime (k/sec): (4415223/1960) IV size: 8 bytes replay detection support: Y Status: ACTIVE outbound ah sas: outbound pcp sas:Next, we would try to Ping and watch the encaps/decaps field
R2(config-if)#do ping 192.168.3.1 sou lo0Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds:Packet sent with a source address of 192.168.2.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 176/356/552 msR2(config-if)#do sh cry ipsec sainterface: Serial0/0 Crypto map tag: GETVPN, local addr 172.16.24.2 protected vrf: (none) local ident (addr/mask/prot/port): (192.168.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (192.168.0.0/255.255.0.0/0/0) current_peer 172.16.14.1 port 848 PERMIT, flags={} #pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5 #pkts decaps: 5, #pkts decrypt: 5, #pkts verify: 5 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.16.24.2, remote crypto endpt.: 172.16.14.1 path mtu 1500, ip mtu 1500, ip mtu idb Serial0/0 current outbound spi: 0x38FEDAF9(956226297) inbound esp sas: spi: 0x38FEDAF9(956226297) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 5, flow_id: SW:5, crypto map: GETVPN sa timing: remaining key lifetime (k/sec): (4415222/1920) IV size: 8 bytes replay detection support: Y Status: ACTIVE inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0x38FEDAF9(956226297) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 6, flow_id: SW:6, crypto map: GETVPN sa timing: remaining key lifetime (k/sec): (4415222/1917) IV size: 8 bytes replay detection support: Y Status: ACTIVE outbound ah sas: outbound pcp sas:The icmp packets are encrypted in IPSEC
R2(config-if)#do sh cry isa saIPv4 Crypto ISAKMP SAdst src state conn-id slot status172.16.14.1 172.16.24.2 GDOI_IDLE 1003 0 ACTIVEIPv6 Crypto ISAKMP SAOn the server.
R1#sh cry gdoiGroup Information Group Name : VPN Group Identity : 1 Group Members Registered : 2 Group Server : Local Group Rekey Lifetime : 86400 secs Rekey Retransmit Period : 10 secs Rekey Retransmit Attempts : 3 IPSec SA Number : 10 IPSec SA Rekey Lifetime : 3600 secs Profile Name : GETVPN SA Rekey Remaining Lifetime : 3010 secs access-list 103 permit ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255 Group Member List for Group VPN : Member ID : 172.16.24.2 Member ID : 172.16.34.3Everything is up and running. :-)I have already posted on EZVPNS, so the only VPN configuration left is the SSL VPN. I would try to get that done in the coming week. :-)
Ciao.
Amplebrain.
 Test connectivity to the internal network..
Test connectivity to the internal network..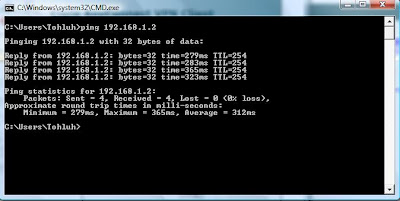 But connectivity to the local LAN is lost...
But connectivity to the local LAN is lost...